Keeping Windows 8.1 Safe and Secure
- 11/15/2013
- Understanding the UAC
- Changing the UAC level
- Using the Windows Firewall
- Turning Windows Firewall off or on
- Customizing the list of allowed apps
- Adding new apps to the allowed list
- Removing apps from the allowed list
- Restoring the Windows Firewall default settings
- Using Windows Defender
- Removing quarantined files
- Improving your password habits
- Reasons to consider commercial security solutions
- Key points
Removing quarantined files
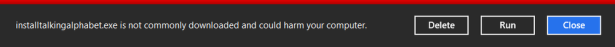
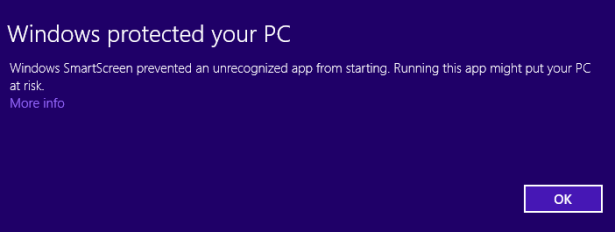
Windows Defender automatically scans all the files and folders through which you browse. If a threat is identified, it is immediately quarantined, and you are informed of this action.
Each time you see a warning similar to the following one, Windows Defender cleaned some threats it detected.
Detected threats are automatically isolated and placed into quarantine. You can only access the items that were quarantined from Windows Defender and decide whether you want to remove them completely from your system or keep them and set Windows Defender to allow them. However, to remove them or keep them you need to have administrator permissions.
In this exercise, you’ll learn how to access the items that were detected as malicious by Windows Defender and remove them from your computer.
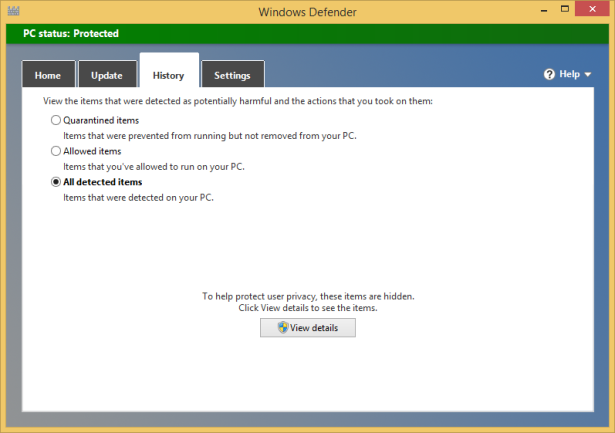
Click the History tab.
Choose All Detected Items.
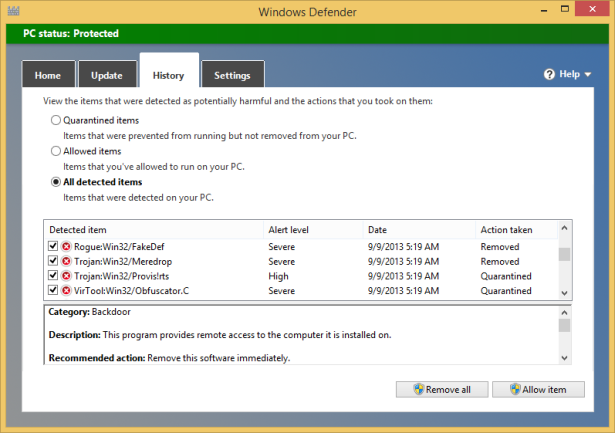
Click View Details to see all the items that were detected as malware.
Scroll through the infected items that were detected and read the information being displayed, to learn more about them.
Click Remove All.
All the items that were detected as threats have now been completely removed from your computer.